Defense in depth
Each layer can implement one or more of the CIA concerns.
| # | Ring | Example | Principle |
|---|---|---|---|
| 1 | Data | Data encryption at rest in Azure blob storage | Integrity |
| 2 | Application | SSL/TLS encrypted sessions | Integrity |
| 3 | Compute | Regularly apply OS and layered software patches | Availability |
| 4 | Network | Network security rules | Confidentiality |
| 5 | Perimeter | DDoS protection | Availability |
| 6 | Identity & Access | Azure Active Directory user authentication | Integrity |
| 7 | Physical Security | Azure data center biometric access controls | Confidentiality |
Infra protection
Management groups are an additional hierarchical level recently introduced into the RBAC model. Management groups add the ability to group subscriptions together and apply policy at an even higher level.
Service Principal is an identity that is used by a service or application. Like other identities, it can be assigned roles.
External Network protection
Application Gateway is a Layer 7 load balancer that also includes a web application firewall (WAF) to provide advanced security for your HTTP-based services. The WAF is based on rules from the OWASP 3.0 or 2.2.9 core rule sets, and provides protection from commonly known vulnerabilities such as cross-site scripting and SQL injection.
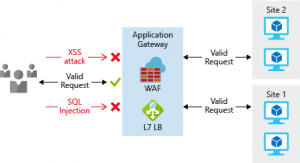
Network virtual appliances (NVA) for non HTTP can be used to secure your network resources. NVAs are similar to firewall appliances you might find in on-premises networks, and are available from many of the most popular network security vendors.
Virtual network security
For communication between virtual machines, network security groups are a critical piece to restrict unnecessary communication.
Virtual network service endpoints are for isolating Azure services to only allow communication from virtual networks
Security Development Lifecycle