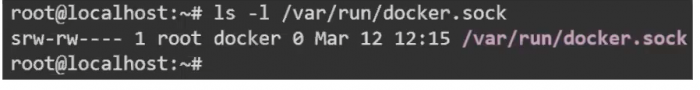
Containers vs Virtual Machines
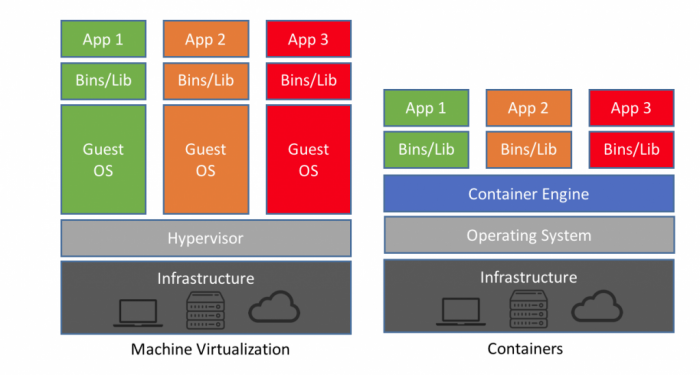
Basics:
- Los procesos deben correr como si estuvieran en otra computadora (process namaspace)
- Idem IPs (network namespace)
- Usuarios diferentes (user namespace)
- Las resouces debe ser limitadas (cgroups)
- No deberias poder escapar el container al host (seccomp-bpf)
Namespace wraps a global system resource in an abstraction
Reference: https://jvns.ca/blog/2016/10/10/what-even-is-a-container/
Como hay muchas formas de hacer containers se creo la OCI (para especificar runtime e imagenes):

La forma más comun de correr container es con Docker:
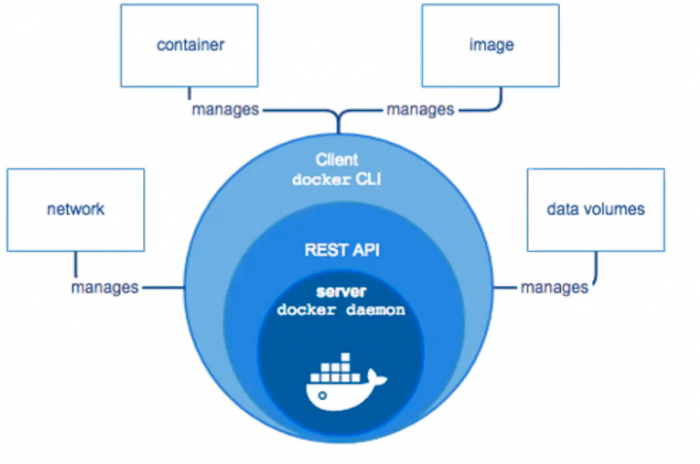

- docker image
- docker inspect (para saber que tiene adentro)
- docker network
- docker exec -it 9288919821 /bin/sh (para ejecutar bash)
Common missconfigurations:
- Mounting docker socket (if an attacker compromises the container can take over the host)
- Como? Start a privileged docker and scape
- Como 2? usar una backdored image
- Exposed docker socket. (lo mismo). Pero igual es una forma de escalar privilegios si estas como local user.
- Si eres local tienes que definir el docker host con: “export DOCKER_HOST=tcp://127.0.0.1:port”. El puerto normal es 2375
- Despues de eso montas root (docker run -it /:/host container_name bash)
- y escapas con chroot (chroot /host bash)
- Privileged container (containe rrunning with privleged option)
- Como? mount host filesystem and use chroot to access host
- Para checarlo: “capsh –print” y revisas si tienes cap_sys_admin
- Shared Network Namspaces
- Como? pivot from one container to another via network
- Excesive linux capabilities like (cap_net_raw, cap_sys_admin, cap_setuid, cap_sys_module, cap_sys_ptrace, cap_dac_read_search, dac_override) examples can be found here https://github.com/Mexican-Pentester/Container_CAP_Explotation
- Containerd demon is running in the host machine
- ctr run –priviliged –net-host …etc.. bash
- Abusing runc same ^
- Insecure docker registry (docker registry is where you save images)
- by checking vuln in the images
- by overwriting images with malware
- El puerto normal es 5000
Kubernetes
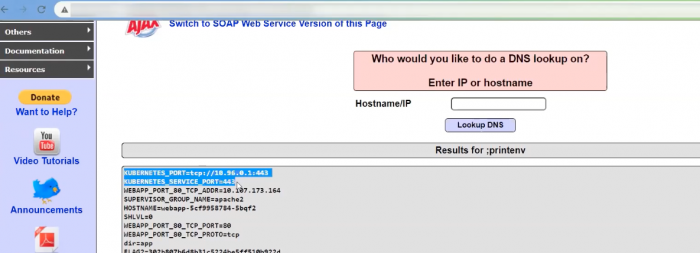
In this part of the course he uses Multillidae to see the environment variables with
kubectl exec -it container -- sh /# printenv
The output shows that certain environment variables have been assigned the values of Pod fields:
MY_POD_SERVICE_ACCOUNT=default ... MY_POD_NAMESPACE=default MY_POD_IP=172.17.0.4 ... MY_NODE_NAME=minikube ... MY_POD_NAME=dapi-envars-fieldref
After we have to change the mount
mount
That will show you i fhtere is something like /secrets/ there
/run/secrets/kubernetes.io/serviceaccount
From there we can list them
ls -l /run/secrets/kubernetes.io/serviceaccount
Si encuentras un kubectl local que no se puede executar lo puedes copir a tu user (por ejemplo data) y ejecutrarlo
Con el token que encontraste en mount puedes hablar con kubectl 🙂
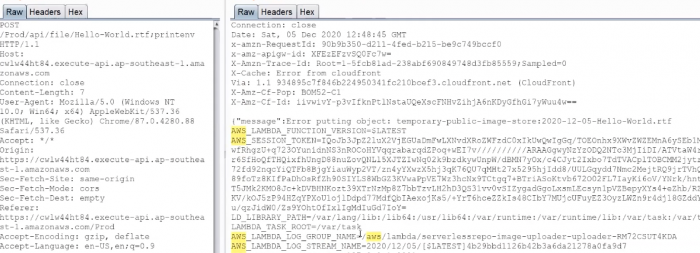
Como lambda es un container tambien puedes printenv
Docker Host Security
- Check permissions of UNIX socket (ls -l var/run/docker.sock)
- TCP is only listening locally or you have authentication (netstat -tpln)
- Check docker group (cat etc/group | grep docker)
- Insecure registries (cat /etc/docker/daemon.json)
- capsh to check for capabilities (capsh –print)
Tools Scanning and benchmark
- Docker Bench for Security https://github.com/docker/docker-bench-security
- Dockscan (is olllddddd) https://github.com/kost/dockscan
- Amicontained https://github.com/genuinetools/amicontained. –> puede correr dentro del container
- docker file lint (docker file installer) https://github.com/replicatedhq/dockerfilelint
- Clair (know vulnerabilities in images) https://github.com/quay/clair
- Docker hub can also scan using Synk
Tools privilage escalation
- Dockerrootplease https://hub.docker.com/r/chrisfosterelli/rootplease/
- Docker-rootshell https://github.com/gtank/docker-rootshell
https://www.marcolancini.it/2018/blog-arsenal-cloud-native-security-tools/#docker
For monitoring/loging Falco with local agents (elasticsearch and kibana) https://hub.docker.com/r/falcosecurity/falco